By the time you complete this article, there will have been about 15 ransomware attacks – almost one every 10 seconds. And our nation’s hospitals are the primary target.
Ransomware attacks against healthcare providers are becoming more prevalent. In fact, one of the largest attacks in US history happened last month, and just this week, a rare tri-agency ransomware high alert was issued by the FBI, HHS, and CISA. There have been credible reports of a Russian-based cyber-crime operation known as Ryuk planning to deploy targeted ransomware at more than 400 healthcare facilities in the US. However, the potential harm to patient care, the operational damage to a Covid-19-strained healthcare system, the loss of information critical to saving lives, and the astronomical recovery costs can be catastrophic. In the most critical cases, an attack can effectively bring the hospital’s entire system down. Such an event can result in the cancellation of scheduled surgeries, ambulances rerouting, or critical patients being transferred to another facility and or provider mid-treatment.
The sad truth is that ransomware attacks are happening and will continue to happen. While we can’t say for certain whom a hacker will target, or when, it has become necessarily critical for healthcare and life sciences organizations to take a proactive security-by-design approach to better understand, assess and prevent the threat of ransomware, and to minimize the overall impact.
Trends Tell a Story
In July of 2020, somebody compromised over 1 million patient healthcare records. The very next month, this number almost doubled. By September, bad actors compromised over 9.5 million patient records in a series of 88 breaches in Q3 alone. While our healthcare systems’ vulnerability operating under strain due to Covid-19 attracts cybercriminals, healthcare organizations can do more to protect themselves by first understanding how attacks occur.
Our team evaluated the trends of U.S. healthcare security incidents over the past 12 months. Our analysis revealed that most security incidents during this period resulted from hacking – over 350 attacks compromising 21.7 million records according to the Wall of Shame from the Office of Civil Rights. Criminals are always searching for attack vectors – or open doors – to get PHI. For most hospitals, recently, that open door has been through phishing attempts. These are emails made to look like legitimate communications with links that launch malware when clicked. The attacks are getting increasingly sophisticated and more convincing.
Assessing Your Target Points
Knowledge is the key to success. The first step toward breach preparedness is to uncover where the sensitive data (PHI and PII) lives. Regardless of whether the answer is ‘in the cloud’ or ‘on-premises,’ a thorough assessment resulting in a comprehensive PHI inventory is necessary. You cannot protect your data if you don’t know where it is.

Heard at HLTH 2024: Insights from Innovative Healthcare Executives
Executives from Imagine360, Verily, BrightInsight, Lantern, and Rhapsody shared their approaches to reducing healthcare costs and facilitating digital transformation.
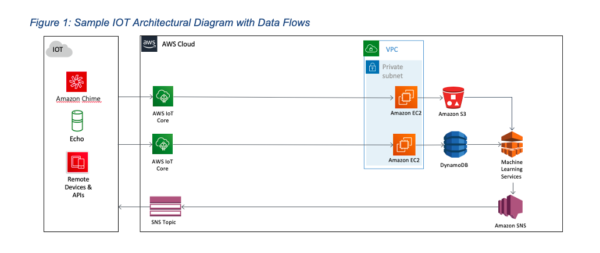
It isn’t easy to defend your environment in that same spirit if you don’t know what it is. Understanding the architecture of an environment can be a useful and valuable artifact. Indeed it may be critical to responding to security or operational incidents. A typical architectural diagram visually explains, for example, where a database may be in relation to a public-facing web application server, a load balancer, or a storage bucket. It may also depict where specific restrictions are applied or not. Periodically this artifact should be updated to reflect new elements added or removed from the system.
Layering the designed data flow through the environment is also critical to understanding where one should deploy enhanced safeguards. Protecting data throughout its lifecycle is a mandate by patients and by regulators. Data flow documentation helps an organization understand more about its data throughout that lifecycle. (click graphic to enlarge)
Prevention Strategies
In a joint alert, the Department of Homeland Security Cybersecurity and Infrastructure Agency, the FBI, and the Department of Human Services shed light on the recent Ryuk / Trickbot threat and what entities must do to manage the risk of ransomware and other cybercrimes. They stated:
“The only way to stop ransomware attacks is to prohibit the payment of ransom demands. If the flow of cash stops, the attacks will stop, and patients will not be put at risk. It’s as simple as that.”
While this has merit, I also recommend focusing on five immediately actionable to-dos healthcare organizations can implement to help mitigate the risk of becoming a target and to lessen the impact should that day come.
I. Backup & disaster recovery:
- Make sure you are backing up your critical systems and your sensitive data.
- Test those backups to make sure somebody can restore them.
- Perform regular data integrity tests.
- Be sure backups are isolated from computing resources.
- Offload backups to an environment that is completely isolated from the live environment.
- Identity recovery time and recovery point objectives.
- Practice your resiliency plans so that you are not caught flat-footed in a crisis.
II. Email security training:
- Conduct regular security awareness training to emphasize current threats, such as phishing schemes.
III. Access controls:
- Disable files running from AppData/LocalAppData folders.
- If possible, disable remote desktop protocols (RDP).
- Limit end-user access to mapped drives
- Deploy firewalls and block Tor, I2P and restrict specific ports
IV. Compute hardening:
- Harden your compute instances by turning off unused services and closing ports
- Leverage CIS hardening benchmarks regularly to fortify your virtual machines
- Patch your environment on a regular basis
- Stay away from end-of-life operating systems and software that cannot be maintained
V. Vulnerability management:
- Make sure to install anti-malware defenses in your environment – and double-check to make sure those defenses are configured correctly.
- Keep anti-malware software up-to-date.
- Perform regular environment scans of your environment to and act on the vulnerabilities revealed.
- Security risk assessment: have a third-party expert perform at least an annual security risk assessment that meets or exceeds HIPAA requirements.
The need to protect patient data is more critical than ever before, and we cannot allow ransomware attacks to impede our ability to provide care to patients where every minute matters. I see the best path forward for healthcare organizations as first to understand the characteristics, causes, and indicators of ransomware attacks and then be proactive in taking preventative measures. Healthcare organizations today must develop a contingency plan, test that plan, and accept they will need to use it. When it comes to healthcare, data held ransom can mean lives are lost, and patients die.
Most cybercriminals are looking for easy prey. Let’s boost our collective defenses and make it harder for them so we can begin to eradicate this plague they have placed upon our healthcare system. We cannot allow cybercriminals to continue to attack our healthcare infrastructure. The time for action was yesterday.
Photo: kentoh, Getty Images
Chris Bowen is an accomplished executive with over 20 years of experience in healthcare technology, security, and privacy. Bowen’s expertise spans multiple public cloud platforms and is known for his passion for protecting patient privacy and ensuring health data security. He is a sought-after speaker at national industry events and webinars on topics spanning health data security, legislation, and AI in healthcare.
This post appears through the MedCity Influencers program. Anyone can publish their perspective on business and innovation in healthcare on MedCity News through MedCity Influencers. Click here to find out how.